New CS0-001 Dumps - Pass CompTIA CySA+ Certification Exam Easily In 2020
CS0-001 exam, which is for CompTIA CySA+ certification, is not an easy task, but we promise, you can pass your CS0-001 exam now. We newly updated CompTIA CySA+ certification CS0-001 exam dumps on 2/7/2020, which can be your passport of CompTIA CySA+ Certification Exam. Now, CS0-001 exam dumps V14.02 is available with 414 practice questions and answers. If you have purchased our dumps before, please check and if different, just contact us for the new version. If you are new who want to get the New CS0-001 Dumps to pass CompTIA CySA+ Certification Exam Easily In 2020, just purchase directly. Including new CS0-001 dumps, we also have some key questions of CS0-001 and CompTIA CySA+ certification for you.

Compare to other related certification, CompTIA CySA+ is different
It must be clear that CompTIA Cybersecurity Analyst (CySA+) is an IT workforce certification that applies behavioral analytics to networks and devices to prevent, detect and combat cybersecurity threats. We have data that over 1.3 million CompTIA ISO/ANSI-accredited exams have been delivered since January 1, 2011. Comparing with other related certification, such as EC-Council Certified Security Analyst (ECSA), GIAC Continuous Monitoring Certification (GMON) and Certified Information Systems Auditor (CISA), why CompTIA CySA+ is different? You can read the content of the following picture:
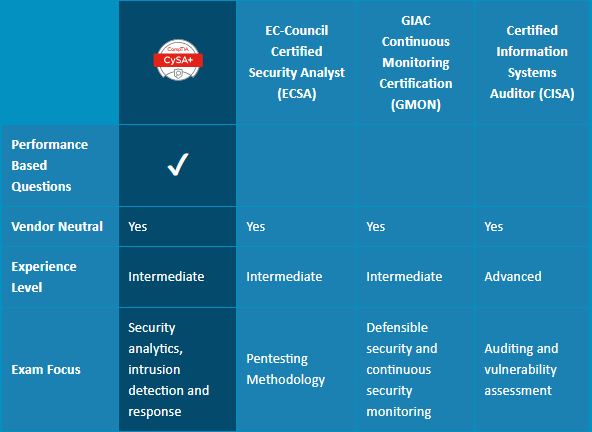
From this picture, you can find CompTIA CySA+ certification is an intermediate level exam which focuses on security analytics, intrusion detection and response. Actually, CompTIA CySA+ certification is for IT professionals
looking to gain the following security analyst skills:
● Perform data analysis and interpret the results to identify vulnerabilities, threats and risks to an organization.
● Configure and use threat-detection tools.
● Secure and protect applications and systems within an organization.
General speaking, CompTIA CySA+ is the only intermediate high-stakes cybersecurity analyst certification with performance-based questions covering security analytics, intrusion detection and response. High-stakes exams are proctored at a Pearson VUE testing center in a highly secure environment. And it is the most up-to-date security analyst certification that covers advanced persistent threats in a post-2014 cybersecurity environment.
CompTIA CS0-001 Exam Will Retire in October of 2020, New CompTIA CySA+ CS0-002 Exam Coming In Q2, 2020
You need to prepare for CS0-001 and write it for your CompTIA CySA+ certification as soon as possible. We checked CS0-001 exam will retire in October of 2020, and new CompTIA CySA+ CS0-002 Exam coming In Q2, 2020. In detail, CS0-002 will be available in April of 2020.
What is the difference between CS0-001 and CS0-002?

The CompTIA Cybersecurity Analyst (CySA+) certification CS0-001 exam mainly verifies that successful candidates have the knowledge and skills required to configure and use threat detection tools, perform data analysis and interpret the results to identify vulnerabilities, threats and risks to an organization, with the end goal of securing and protecting applications and systems within an organization.
And the CompTIA Cybersecurity Analyst (CySA+) certification CS0-002 exam mainly verifies that successful candidates have the knowledge and skills required to leverage intelligence and threat detection techniques, analyze and interpret data, identify and address vulnerabilities, suggest preventative measures, and effectively respond to and recover from incidents.
Additionally, CS0-001 exam is related to Network+, Security+ or equivalent knowledge. Minimum of 3-4 years of hands-on information security or related experience. While there is no required prerequisite, CySA+ is intended to follow CompTIA Security+ or equivalent experience and has a technical, hands-on focus. However, CS0-002 exam is for Network+, Security+ or equivalent knowledge. Minimum of 4 years of hands-on information security or related experience.
New CS0-001 Dumps Come With CS0-001 Free Dumps, You Can Check Before Writing CS0-001 Dumps
It is highly recommended to read free demo questions before get CS0-001 exam dumps. New CS0-001 dumps from DumpsBase come with CS0-001 free dumps as below, you can check before writing CS0-001 dumps.
A security analyst is adding input to the incident response communication plan. A company officer has suggested that if a data breach occurs, only affected parties should be notified to keep an incident from becoming a media headline.
Which of the following should the analyst recommend to the company officer?
A. The first responder should contact law enforcement upon confirmation of a security incident in order for a forensics team to preserve chain of custody.
B. Guidance from laws and regulations should be considered when deciding who must be notified in order to avoid fines and judgements from non-compliance.
C. An externally hosted website should be prepared in advance to ensure that when an incident occurs victims have timely access to notifications from a non-compromised recourse.
D. The HR department should have information security personnel who are involved in the investigation of the incident sign non-disclosure agreements so the company cannot be held liable for customer data that might be viewed during an investigation.
Answer: A
A company has recently launched a new billing invoice website for a few key vendors. The cybersecurity analyst is receiving calls that the website is performing slowly and the pages sometimes time out. The analyst notices the website is receiving millions of requests, causing the service to become unavailable.
Which of the following can be implemented to maintain the availability of the website?
A. VPN
B. Honeypot
C. Whitelisting
D. DMZ
E. MAC filtering
Answer: C
An analyst has initiated an assessment of an organization’s security posture. As a part of this review, the analyst would like to determine how much information about the organization is exposed externally.
Which of the following techniques would BEST help the analyst accomplish this goal? (Select two.)
A. Fingerprinting
B. DNS query log reviews
C. Banner grabbing
D. Internet searches
E. Intranet portal reviews
F. Sourcing social network sites
G. Technical control audits
Answer: DF
A cybersecurity professional typed in a URL and discovered the admin panel for the e-commerce application is accessible over the open web with the default password.
Which of the following is the MOST secure solution to remediate this vulnerability?
A. Rename the URL to a more obscure name, whitelist all corporate IP blocks, and require two-factor authentication.
B. Change the default password, whitelist specific source IP addresses, and require two-factor authentication.
C. Whitelist all corporate IP blocks, require an alphanumeric passphrase for the default password, and require two-factor authentication.
D. Change the username and default password, whitelist specific source IP addresses, and require two-factor authentication.
Answer: D
An organization is requesting the development of a disaster recovery plan. The organization has grown and so has its infrastructure. Documentation, policies, and procedures do not exist.
Which of the following steps should be taken to assist in the development of the disaster recovery plan?
A. Conduct a risk assessment.
B. Develop a data retention policy.
C. Execute vulnerability scanning.
D. Identify assets.
Answer: D
A company wants to update its acceptable use policy (AUP) to ensure it relates to the newly implemented password standard, which requires sponsored authentication of guest wireless devices.
Which of the following is MOST likely to be incorporated in the AUP?
A. Sponsored guest passwords must be at least ten characters in length and contain a symbol.
B. The corporate network should have a wireless infrastructure that uses open authentication standards.
C. Guests using the wireless network should provide valid identification when registering their wireless devices.
D. The network should authenticate all guest users using 802.1x backed by a RADIUS or LDAP server.
Answer: C
An analyst was tasked with providing recommendations of technologies that are PKI X.509 compliant for a variety of secure functions.
Which of the following technologies meet the compatibility requirement? (Select three.)
A. 3DES
B. AES
C. IDEA
D. PKCS
E. PGP
F. SSL/TLS
G. TEMPEST
Answer: BDF
An organization has recently recovered from an incident where a managed switch had been accessed and reconfigured without authorization by an insider. The incident response team is working on developing a lessons learned report with recommendations.
Which of the following recommendations will BEST prevent the same attack from occurring in the future?
A. Remove and replace the managed switch with an unmanaged one.
B. Implement a separate logical network segment for management interfaces.
C. Install and configure NAC services to allow only authorized devices to connect to the network.
D. Analyze normal behavior on the network and configure the IDS to alert on deviations from normal.
Answer: B
A cybersecurity analyst is reviewing the current BYOD security posture. The users must be able to synchronize their calendars, email, and contacts to a smartphone or other personal device. The recommendation must provide the most flexibility to users.
Which of the following recommendations would meet both the mobile data protection efforts and the business requirements described in this scenario?
A. Develop a minimum security baseline while restricting the type of data that can be accessed.
B. Implement a single computer configured with USB access and monitored by sensors.
C. Deploy a kiosk for synchronizing while using an access list of approved users.
D. Implement a wireless network configured for mobile device access and monitored by sensors.
Answer: D
A security analyst received a compromised workstation. The workstation’s hard drive may contain evidence of criminal activities.
Which of the following is the FIRST thing the analyst must do to ensure the integrity of the hard drive while performing the analysis?
A. Make a copy of the hard drive.
B. Use write blockers.
C. Run rm –R command to create a hash.
D. Install it on a different machine and explore the content.
Answer: B
File integrity monitoring states the following files have been changed without a written request or approved change.
The following change has been made:
chmod 777 –Rv /usr
Which of the following may be occurring?
A. The ownership pf /usr has been changed to the current user.
B. Administrative functions have been locked from users.
C. Administrative commands have been made world readable/writable.
D. The ownership of/usr has been changed to the root user.
Answer: C
A security analyst has created an image of a drive from an incident.
Which of the following describes what the analyst should do NEXT?
A. The analyst should create a backup of the drive and then hash the drive.
B. The analyst should begin analyzing the image and begin to report findings.
C. The analyst should create a hash of the image and compare it to the original drive’s hash.
D. The analyst should create a chain of custody document and notify stakeholders.
Answer: C
A cybersecurity analyst is currently investigating a server outage.
The analyst has discovered the following value was entered for the username: 0xbfff601a.
Which of the following attacks may be occurring?
A. Buffer overflow attack
B. Man-in-the-middle attack
C. Smurf attack
D. Format string attack
E. Denial of service attack
Answer: D
External users are reporting that a web application is slow and frequently times out when attempting to submit information.
Which of the following software development best practices would have helped prevent this issue?
A. Stress testing
B. Regression testing
C. Input validation
D. Fuzzing
Answer: A
We also will crack new CS0-002 dumps once it is available. You can trust DumpsBase for your CompTIA CySA+ Certification Exam.
